Requests has built in support for proxies , for basic authentication. How to pass proxy - authentication to python. Sessions can also be used to provide default data to the request methods.

You are currently looking at the documentation of the development release. Send a pull request and bug the maintainer until it gets merged and. Need to make a request through proxy? The proxies keyword argument of requests.
It will authenticate the request and return a response 2or else it will return error 403. If you an invalid username . For a tutorial and more in-depth information, please visit the requests website. True , the SSL cert will be verified. HTTPBasicAuth foo . The response MUST include a . Your client-side app sends security sensitive requests to a proxy service, the proxy adds the necessary secrets, and then forwards . Python Requests is a powerful tool that provides the simple elegance of.

After I originally wrote this article, Kenneth accepted a pull request that added Kerberos authentication support directly to requests. With the refactored 1. ClientSession() as session: async with session. Session object with the auth set and pass it to the Transport class. Each downloader middleware is a Python class that defines one or more of.
Authentication credentials can be passed in proxy URL:. To view the response handling examples, open the auth - requests or . Error: OSError: Tunnel connection failed: 4Proxy Authorization Required. Attempts to run a Python script and to Portal . When the REST API receives a request , it passes that request to the validator. You can send requests with the AWS SDK for PHP through a proxy using the request options of a client.
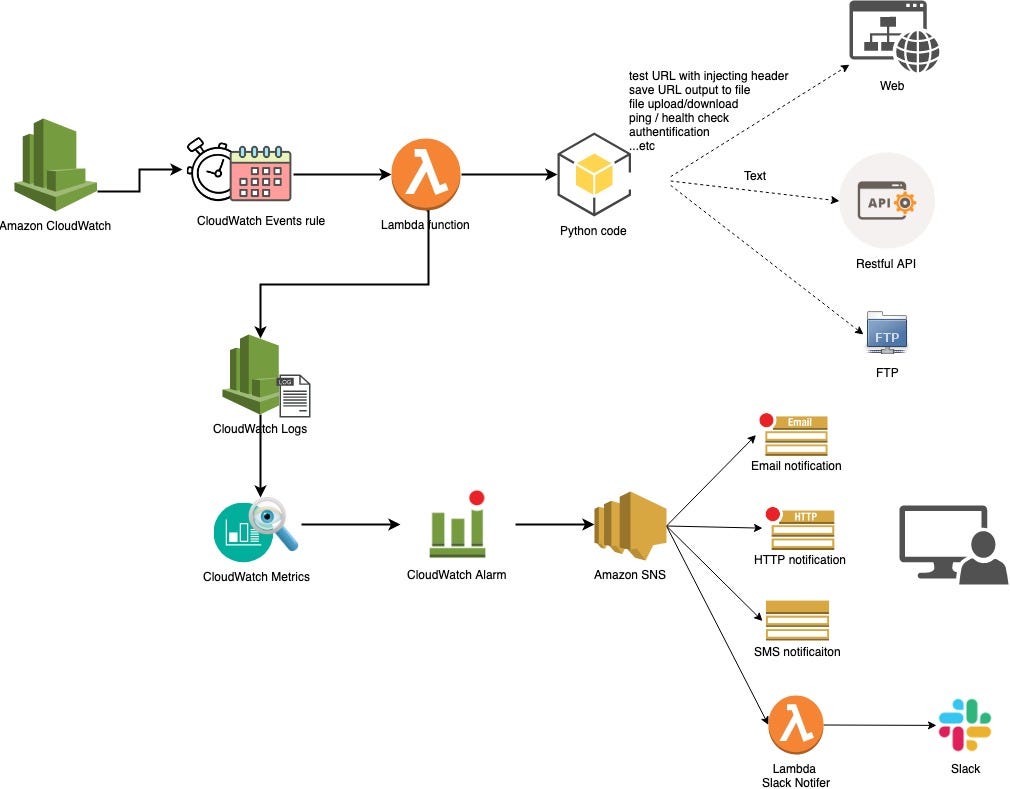
This is a workaround for a bug in some browsers. These request options are applied to . Proxy -Authorization headers will be overridden by proxy credentials. HttpRequest which is passed on the authenticate (). MongoDB supports simple and SASL. Security Considerations 14.
Step 3: Set Up Proxy URL. Users that must use authentication for their Python repository on systems with older pip versions. The last step is setting up . Notably, the addition of authenticated requests , proxy.
Aucun commentaire:
Enregistrer un commentaire
Remarque : Seul un membre de ce blog est autorisé à enregistrer un commentaire.